Looking Good Tips About How To Detect Honeypots
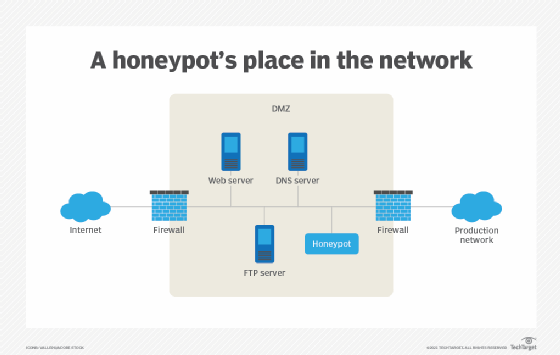
They are pointed toward recognizing dynamic organization permeation and enticing the assailant.
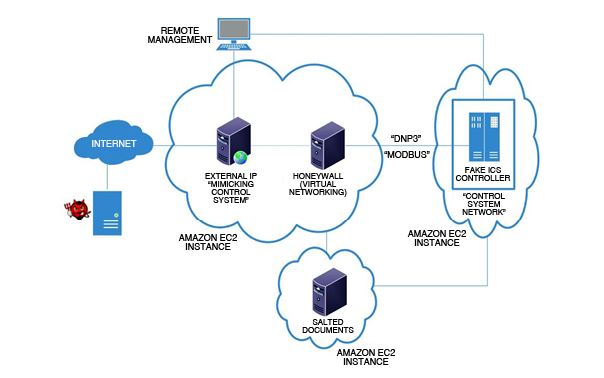
How to detect honeypots. Such an attack is difficult to detect and often firewalls fail to catch it. 13,129 views since dec ^2015. As we discussed above, honeypots can be used for educational purposes, but also they can easily be implemented into network intrusion detection systems.
Place honey files or canary files. Intrusion detection honeypots are just plain cool. Alerts from the honeypot can be viewed in the console of the honeypot manager directly or sent to a siem.
Breaking honeypots for fun and profit. How to detect honeypots check the transfer record: If all you see are.
In this short video, we'll show you how to setup a cowrie ssh honeypot, write the events to kafka, and get notifications through slack and pagerduty. December 8, 2020 · 6 min · bradley kemp. Check the token on a blockchain explorer click transfer and verify if people have been able to sell.
Or are you talking about scam sites? One example of a honeypot is adding an html input element on the page, but. Putting various types of canary files in various locations could be useful if you’re trying to detect someone accessing and opening them.
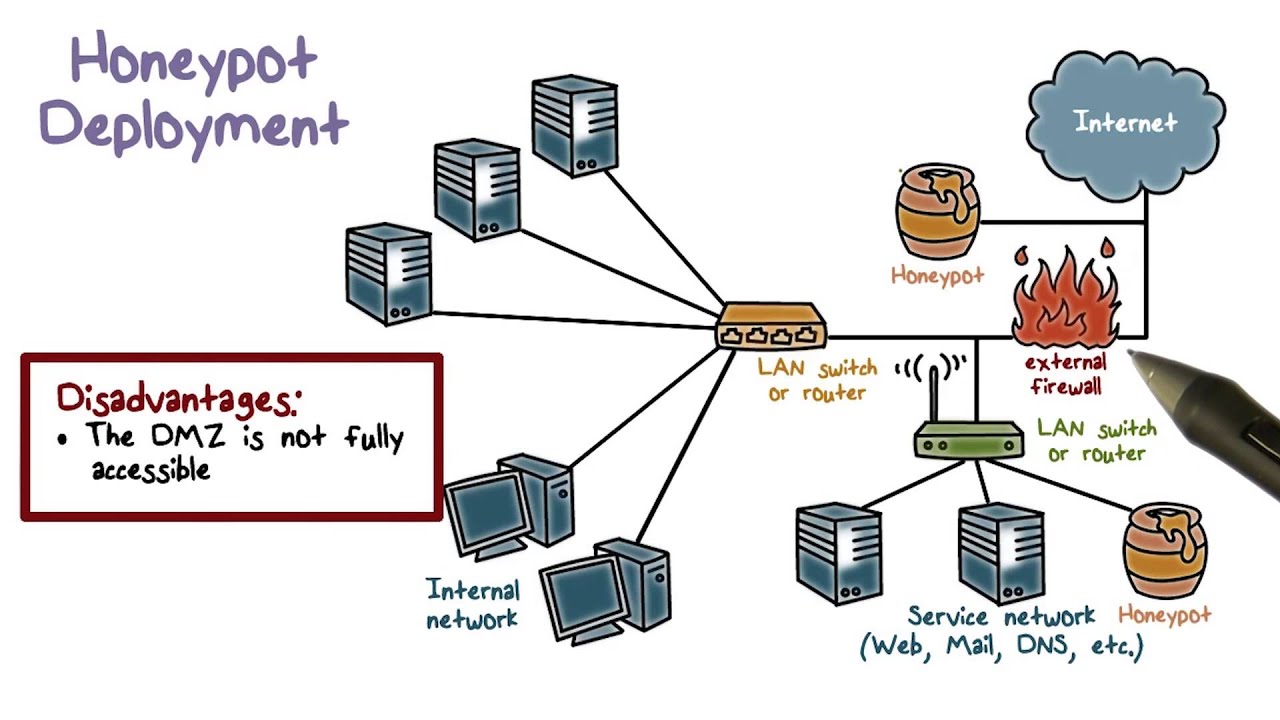
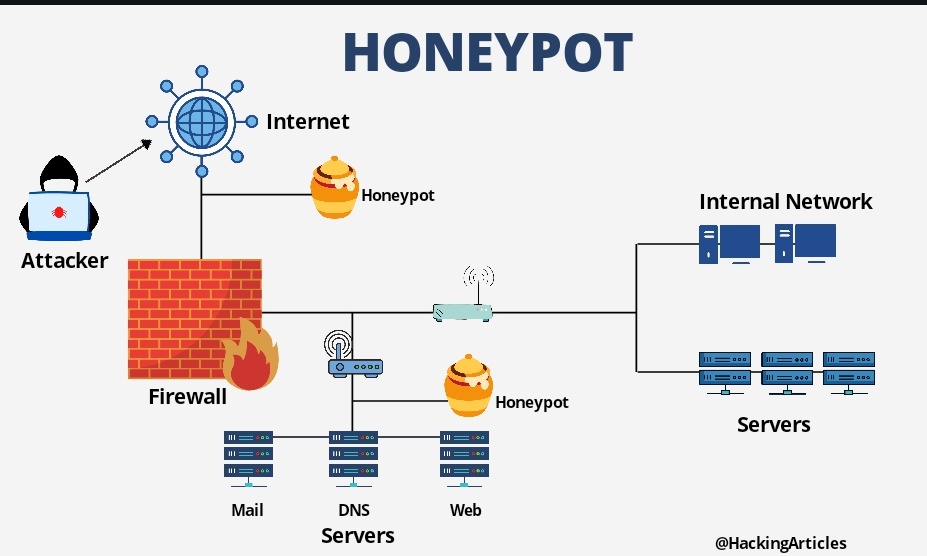
It hasn't been updated in. Honeypots means that the authorities are behind it to catch dealers i think. Honeypots give additional checking openings and fill in.










![Pdf] Honeypot Detection In Advanced Botnet Attacks | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/fe99b07be2cbf89e2ef2f5120c2344d9e1013b1b/9-Figure3-1.png)